Post by : Anis Karim
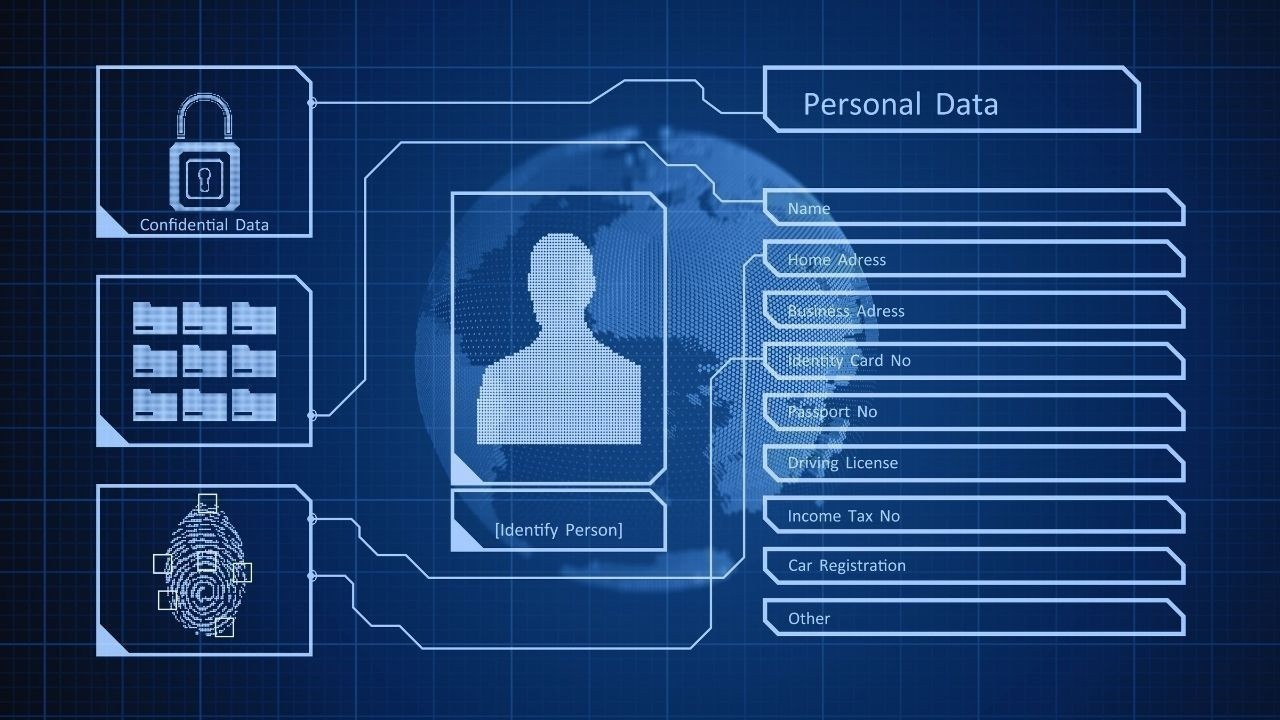
The twin forces of scale and risk are driving digital identity to a tipping point. More services, more users, more devices—all increase the number of identity interactions every day. At the same time, identity systems are under relentless assault: phishing, credential theft, password reuse and sophisticated attacks persist. Traditional username‑password combinations are showing their age.
Organisations are now asking: can we move to a model that is passwordless (so users don’t have to remember or manage credentials), private (so users’ identities aren’t needlessly exposed or tracked) and secure (so attacks are prevented rather than just detected)? These three goals—passwordless, private, secure—are often used together in vendor branding and strategy documents. But achieving them simultaneously is more challenging than it sounds.
Passwordless identity means replacing or eliminating the “something you know” secret (password) with either “something you have” (device, token) or “something you are” (biometrics) or a combination thereof. In effect, you no longer rely on the user remembering or typing a secret that might be stolen, guessed or reused. This reduces many common attack surfaces. pingidentity.com+2Microsoft Learn+2
Privacy in identity systems means that users’ personal data and biometric templates are not unnecessarily stored or shared, and identity verification is done in a way that minimises the amount of data transferred or held by third parties. It also means giving users control of their identity attributes—deciding what to share and with whom. Keyless+1
Security means the identity system resists known threats—credential stuffing, phishing, replay attacks, supply‑chain compromise—and remains resilient. It also implies standards, auditability, encryption, device binding, and operational maturity. RSA
While each of these is important on its own, the real challenge lies in implementing an identity solution that truly delivers on all three simultaneously.
Standards like WebAuthn, FIDO2 and passkeys are gaining traction. These move away from passwords toward cryptographic keys bound to devices and unlocked by biometrics or PINs. Because no password is stored on servers, phishing resistance goes up significantly. FIDO Alliance+2Microsoft Learn+2 Organisations adopting these see reduced help‑desk loads, fewer password reset requests and a smaller attack surface.
Traditional identity systems are centralised: credentials managed by a service provider, identity attributes stored in databases controlled by third parties. Newer models aim for self‑sovereign identity (SSI): users control their identity attributes, share only what’s needed, and verification is done without exposing unnecessary data. Studies show that decentralised biometric authentication protocols and attribute‑based encryption are gaining research traction. arXiv+1
Platforms are increasingly promoting biometric authentication where biometric data never leaves the device, or is stored in a way that it cannot be reconstructed or misused. For example, some solutions offer “no biometric data stored anywhere” while enabling face scans, fingerprint verification and passive authentication. Keyless
Identity‑as‑a‑Service platforms are supporting passwordless workflows, device‑binding, biometric integration and consent‑driven attribute sharing. These platforms help organisations move beyond legacy credential systems to modern, secure digital identity. 1Kosmos+1
With increased regulatory scrutiny around identity, privacy and data security (think GDPR, digital identity frameworks, new authentication standards), organisations are under pressure to adopt secure and privacy‑by‑design identity solutions. This is fostering vendor innovation and adoption.
When there are no passwords to steal or reuse, many common attacks become harder or irrelevant. Organisations implementing passkeys or device‑bound credentials report fewer credential theft incidents. pingidentity.com+1
Removing the need to remember passwords or reset them enhances user convenience, reduces friction and improves conversion or engagement. Passkeys specifically claim faster login times and higher success rates. FIDO Alliance+1
Help‑desk costs for password resets, account lockouts and credential management are substantial. Passwordless identity solutions reduce those overheads. pingidentity.com
By shifting identity verification to user‑managed devices and limiting the amount of personal data stored centrally, privacy risks are reduced. This can improve trust, reduce liability and support compliance efforts.
Organisations adopting modern identity solutions are better positioned for evolving threats, new standards, device ecosystems and regulatory changes.
One challenge of device‑bound credentials (passkeys, security keys) is if a user loses their device, gets locked out or needs to switch platforms. Recovery mechanisms become critical. Organisations must ensure fallback paths that do not compromise security or privacy. TechRadar
Many enterprises still rely heavily on old identity systems (password + username, federated login, single sign‑on). Migrating to fully passwordless identity is a complex undertaking: system compatibility, user onboarding, support, training, and change‑management all matter.
While users want convenience, they may not fully understand the implications of device‑bound biometrics, attribute sharing or identity federation. Vendors claiming “no data stored” or “we don’t know who you are” must be audited. The real‑world privacy properties of identity solutions vary widely.
Although passwords may vanish, identity systems still face threats: supply‑chain attacks, compromised hardware, programming errors, new biometric spoofing or side‑channel attacks. Security architectures still need to account for new failure modes.
Although standards such as FIDO2 and WebAuthn exist, real‑world ecosystem support (all services, legacy systems, devices all platforms) is not universal yet. Organisations may face partial implementations that degrade user experience or security.
Even the best identity system can fail if users are not correctly enrolled, devices are mis‑configured, recovery paths are weak or user habits remain insecure. Training, user experience design and support systems remain critical.
Identify where identity risk is highest: remote access, high‑value accounts, customer login, third‑party access. Understand the cost of current identity failures (breaches, lockouts, fraud) and the usability pain points. Use those findings to prioritise deployment of modern identity solutions.
Map out your identity ecosystem: current credential methods, directories, access flows, devices, recovery mechanisms, federation. Define how passwordless, private and secure identity will be introduced—whether via passkeys, device security keys, biometric platforms, credential‑less flows. This roadmap must include legacy system integration and migration.
Select identity solutions that align with open standards (WebAuthn, FIDO2, ISO identity frameworks), support privacy‑preserving architectures (where biometric data stays on device, minimal attribute disclosure) and have rigorous security certifications or audit history.
Design fallback and recovery mechanisms carefully: what if a user loses their device? How will account recovery happen securely and without exposing strong credentials again? How will you handle device lifecycle and revocation?
Track metrics: authentication success rate, time to login, password reset volumes, phishing/fraud incidents, user satisfaction. Use these data to guide further rollout and justify business case.
Communicate clearly with users about how new identity flows work, what’s changing, what’s better and how to manage their devices. User adoption and comfort are major success factors.
Include emerging trends (quantum‑resistant keys, decentralised identity, zero‑trust identity systems) in your strategy to avoid being locked into legacy systems again.
Large service providers are moving toward passkeys as default for new accounts. This represents a shift in the baseline for identity systems. The Verge
SSI and decentralised identity models, based on blockchain, attribute‑based encryption and user‑controlled credentials, will gain more proof‑points and commercial deployment. arXiv
Increasingly, biometric verification will happen entirely on‑device, with no central storage. These architectures will gain traction in sectors with high privacy sensitivity (healthcare, financial services). Keyless
Identity solutions will become more embedded in zero‑trust architecture and identity‑as‑a‑service models, where identity becomes the primary trust mechanism rather than network perimeters.
Regulation around identity, credential management and sensitive personal data will tighten. Identity solutions that deliver strong privacy and audit will have advantage.
As quantum computing advances, identity systems will need to adopt quantum‑resistant key algorithms and architectures—especially for long‑lived credentials and high‑value identity use‑cases. arXiv
The promise of digital identity solutions being passwordless, private and secure is real—and many organisations are making significant progress. The shift away from passwords toward device‑bound cryptographic credentials, user‑managed identity attributes and privacy‑first biometric authentication is underway.
Yet, the trifecta isn’t guaranteed. In practice, trade‑offs exist: legacy systems must be supported, recovery mechanisms must be robust, user behaviours must adapt and security must remain holistic beyond just removing passwords. The most successful identity programmes will treat identity as a strategic asset—not just as credential management—and will build ecosystems where passwords fade out, user privacy improves, and identity attacks become far harder.

Winter Skin Care: 10 Hydrating Drinks That Give Natural Glass Skin Glow
Learn how simple winter drinks keep your skin hydrated reduce dryness and support a natural glass sk

10 Songs That Carry the Same Grit and Realness as Banda Kaam Ka by Chaar Diwari
From underground hip hop to introspective rap here are ten songs that carry the same gritty realisti

PPG and JAFZA Launch Major Tree-Planting Drive for Sustainability
PPG teams up with JAFZA to plant 500 native trees, enhancing green spaces, biodiversity, and air qua

Dubai Welcomes Russia’s Largest Plastic Surgery Team
Russia’s largest plastic surgery team launches a new hub at Fayy Health, bringing world-class aesthe

The Art of Negotiation
Negotiation is more than deal making. It is a life skill that shapes business success leadership dec

Hong Kong Dragon Boat Challenge 2026 Makes Global Debut in Dubai
Dubai successfully hosted the world’s first Hong Kong dragon boat races of 2026, blending sport, cul

Ghanem Launches Regulated Fractional Property Ownership in KSA
Ghanem introduces regulated fractional real estate ownership in Saudi Arabia under REGA Sandbox, ena

Winter Skin Care: 10 Hydrating Drinks That Give Natural Glass Skin Glow
Learn how simple winter drinks keep your skin hydrated reduce dryness and support a natural glass sk

Why Drinking Soaked Chia Seeds Water With Lemon and Honey Before Breakfast Matters
Drinking soaked chia seeds water with lemon and honey before breakfast may support digestion hydrati
Morning Walk vs Evening Walk: Which Helps You Lose More Weight?
Morning or evening walk Learn how both help with weight loss and which walking time suits your body

What Really Happens When You Drink Lemon Turmeric Water Daily
Discover what happens to your body when you drink lemon turmeric water daily including digestion imm

DXB News Network Presents “Ctrl+Alt+Wim”, A Bold New Satirical Series Starring Global Entertainer Wim Hoste
DXB News Network premieres Ctrl+Alt+Wim, a bold new satirical micro‑series starring global entertain

High Heart Rate? 10 Common Causes and 10 Natural Ways to Lower It
Learn why heart rate rises and how to lower it naturally with simple habits healthy food calm routin

10 Simple Natural Remedies That Bring Out Your Skin’s Natural Glow
Discover simple natural remedies for glowing skin Easy daily habits clean care and healthy living ti

Mattel Revamps Masters of the Universe Action Figures for Upcoming Film
Mattel is set to revive Masters of the Universe action figures in sync with their new movie, ignitin