Post by : Anis Karim
Daily, billions engage in personal conversations without a second thought. Topics ranging from health to finances traverse glowing screens, guided by apps that assure users of their safety with jargon that sounds reassuring. One term frequently highlighted is “end-to-end encryption.”
This concept appears formidable and comforting. However, most users fail to grasp that encryption isn’t synonymous with complete security. It doesn’t provide invisibility, legal immunity, or an unyielding barrier against threats.
Rather, end-to-end encryption is a robust tool, but its capabilities have limits.
In an era where privacy is priceless, understanding the true implications of this concept becomes vital. While the technology safeguards messages during transit, it doesn’t necessarily shield you.
Let’s clarify what end-to-end encryption can and cannot achieve, along with the common misconceptions surrounding its effectiveness.
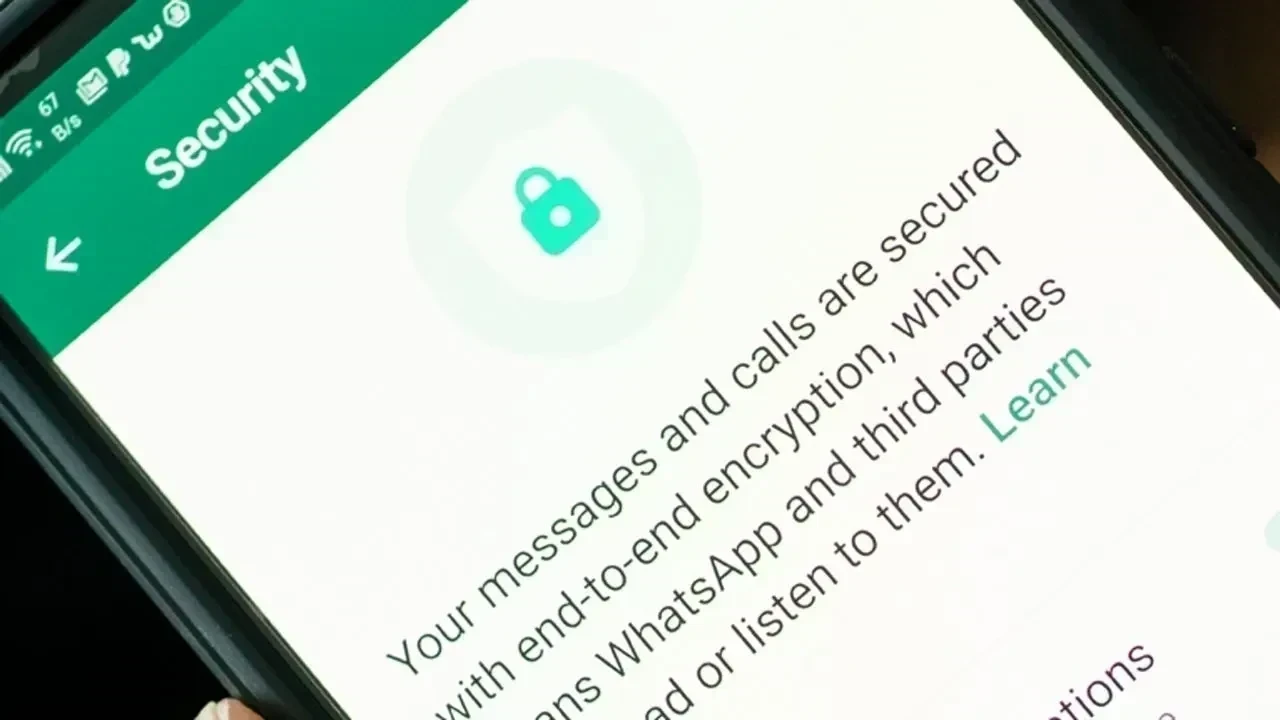
End-to-end encryption denotes the process of converting your message into unreadable code before it exits your device, remaining encrypted until it arrives at the recipient’s device.
Only the sender and the intended receiver possess access to the message:
Not the app.
Not the service provider.
Not potential hackers.
Not even internet service providers.
Ideally.
Visualize placing a letter inside a secure box, locking it, and sending it. The delivery person carries the sealed box but cannot open it; only the recipient with the correct key can unlock it.
This encapsulates the basic principle behind encryption.
When you dispatch a message, numerous behind-the-scenes operations occur:
Your message undergoes mathematical transformation using a key. Without this key, it is rendered as random data.
The encrypted message traverses various networks and servers in an unreadable format.
The receiver's device utilizes a digital key to revert the scrambled message back to its readable form.
During its journey, no one can intercept and interpret it as plain text.
That's the commitment.
Numerous widely-used applications tout end-to-end encryption, such as WhatsApp, Signal, and features embedded in Apple and Google devices.
Each software adopts varied implementations of encryption. Some default to protected chats, while others allow users to opt for encrypted exchanges.
Encryption doesn’t simply act as an on/off switch; it spans a range of security options.
Encryption proves effective against certain threats.
Your messages remain unreadable to hackers monitoring Wi-Fi networks.
Internet service providers cannot inspect the contents of your messages.
Apps themselves cannot access the text of encrypted conversations.
Massive data breaches from servers do not directly compromise message content.
Consequently, encryption plays a crucial role in preserving speech and privacy.
Misunderstandings often crop up here.
While encryption safeguards your messages in transit, it fails to protect against:
• Unauthorized access to your unlocked phone
• Malware on your device
• Spyware that collects your screen activity
• Applications with questionable permissions
• Keyloggers or screen capture software
If your device is compromised, encryption loses its significance.
Because messages are visible on your display.
Numerous users back up chat histories on cloud platforms.
This is where encryption might fail.
Unless encryption for backups is explicitly stated, authorities or malicious entities can access stored chats, even if they cannot read messages in real-time.
Encryption secures content only, not the context.
Data including:
• Who you communicate with
• When you send messages
• Frequency of messages
• Your location
• Device type used
This information is logged.
Metadata can reveal behavior patterns even without inspecting message contents.
In intelligence assessments, metadata can often be more insightful than the messages themselves.
Anyone can take a screenshot of a message.
Encryption doesn’t prevent forwarding.
It doesn’t erase evidence.
If the recipient chooses to save or share the content, privacy can vanish in an instant.
No encryption system operates in a vacuum devoid of human activity.
An impeccably encrypted application is futile if:
• Users fall victim to scams
• Partners misuse their access
• Friends betray trust
• Accounts are hacked
• Passwords are reused
• Devices are irresponsibly shared
Security falters when behavior disregards risk.
Governments frequently express concerns about encryption.
Why?
Because encrypted messages obstruct surveillance.
Authorities contend that criminals exploit private platforms for illicit activities.
Conversely, privacy advocates assert that encryption safeguards ordinary citizens.
Both perspectives coexist.
Encryption itself is neutral.
How it's utilized isn't.
Directly? Rarely.
Indirectly? Often.
They might:
• Request encrypted backups
• Target devices rather than servers
• Access account information
• Monitor metadata
• Employ spyware
• Obtain user credentials
The encryption appears strongest on paper.
In practice, individuals become the targets — not the algorithms.
Trust drives engagement.
Encryption has evolved into:
• A marketing advantage
• A competitive edge
• A privacy assurance
• A shield for reputation
Heightened claims of privacy attract more users.
However, no company can dictate how users act thereafter.
Language surrounding security provides comfort.
Yet absolute safety is an unreachable ideal online.
Encryption complicates breaches but doesn’t eliminate them.
It merely slows down the process.
No, it varies.
Certain apps:
• Offer full encryption
• Do not retain message content
• Limit metadata collection
Others:
• Log user activities
• Store backup data
• Share insights with partners
• Retain transaction records
“Encrypted” does not equate to “private”.
Always verify what additional data is collected.
Truth: Anyone who accesses your device can.
Truth: Metadata speaks volumes.
Truth: Security cannot substitute for sound judgment.
Truth: They nullify encryption entirely.
Truth: It never has.
Encryption is merely a layer, not an entire measure.
Biometric locks offer your first line of defense.
Theft of accounts negates encryption.
Many applications track your behavior unnecessarily.
Cloud configurations often neglect security measures by default.
Encryption is formidable, yet side channels remain.
Digital footprints never fade.
Certain apps claim to offer self-erasing messages.
This doesn't assure complete deletion.
Recipients can:
• Capture screens
• Utilize alternate devices
• Preserve images
• Export their chats
“Vanishing” typically implies disappearing publicly, not privately.
Crucial for:
• Journalists
• Activists
• Whistleblowers
• Political dissidents
• Victims of domestic violence
• Corporate investigators
• Advocates for privacy
It can be a matter of life and death.
For everyday conversations, it safeguards dignity.
Many parents assume encryption offers safety for kids.
Yet, encryption merely conceals actions—it doesn’t assure security.
Children should have:
• Education
• Oversight
• Transparent dialogue
• Digital awareness
Privacy without knowledge cultivates danger.
It secures information.
Not choices.
It guarantees safe transit.
Not relationships.
It conceals content.
Not the results of actions.
Encryption will fortify over time.
However, surveillance tactics will advance as well.
This isn’t a rivalry someone ‘wins’.
It’s an ongoing competition.
Privacy will always be a temporary state.
End-to-end encryption is a remarkable innovation.
It defends expression in an era marked by surveillance.
It fosters liberty in oppressive environments.
It provides dignity in the digital realm.
Yet, it isn’t magical.
It doesn’t eradicate recklessness.
It doesn’t halt screenshots.
It doesn’t shield emotions.
It doesn’t guard against poor choices.
Encryption ensures message safety.
Wisdom safeguards lives.
And in the digital landscape —
Wisdom is the most formidable password you can create.
This article is for informational purposes only and does not serve as legal, cybersecurity, or technical advice. Readers should seek guidance from qualified professionals for personal data protection strategies.

Winter Skin Care: 10 Hydrating Drinks That Give Natural Glass Skin Glow
Learn how simple winter drinks keep your skin hydrated reduce dryness and support a natural glass sk

10 Songs That Carry the Same Grit and Realness as Banda Kaam Ka by Chaar Diwari
From underground hip hop to introspective rap here are ten songs that carry the same gritty realisti

PPG and JAFZA Launch Major Tree-Planting Drive for Sustainability
PPG teams up with JAFZA to plant 500 native trees, enhancing green spaces, biodiversity, and air qua

Dubai Welcomes Russia’s Largest Plastic Surgery Team
Russia’s largest plastic surgery team launches a new hub at Fayy Health, bringing world-class aesthe

The Art of Negotiation
Negotiation is more than deal making. It is a life skill that shapes business success leadership dec

Hong Kong Dragon Boat Challenge 2026 Makes Global Debut in Dubai
Dubai successfully hosted the world’s first Hong Kong dragon boat races of 2026, blending sport, cul

Ghanem Launches Regulated Fractional Property Ownership in KSA
Ghanem introduces regulated fractional real estate ownership in Saudi Arabia under REGA Sandbox, ena

Winter Skin Care: 10 Hydrating Drinks That Give Natural Glass Skin Glow
Learn how simple winter drinks keep your skin hydrated reduce dryness and support a natural glass sk

Why Drinking Soaked Chia Seeds Water With Lemon and Honey Before Breakfast Matters
Drinking soaked chia seeds water with lemon and honey before breakfast may support digestion hydrati
Morning Walk vs Evening Walk: Which Helps You Lose More Weight?
Morning or evening walk Learn how both help with weight loss and which walking time suits your body

What Really Happens When You Drink Lemon Turmeric Water Daily
Discover what happens to your body when you drink lemon turmeric water daily including digestion imm

DXB News Network Presents “Ctrl+Alt+Wim”, A Bold New Satirical Series Starring Global Entertainer Wim Hoste
DXB News Network premieres Ctrl+Alt+Wim, a bold new satirical micro‑series starring global entertain

High Heart Rate? 10 Common Causes and 10 Natural Ways to Lower It
Learn why heart rate rises and how to lower it naturally with simple habits healthy food calm routin

10 Simple Natural Remedies That Bring Out Your Skin’s Natural Glow
Discover simple natural remedies for glowing skin Easy daily habits clean care and healthy living ti

Mattel Revamps Masters of the Universe Action Figures for Upcoming Film
Mattel is set to revive Masters of the Universe action figures in sync with their new movie, ignitin